Cybersecurity Assessments
- FrameworkFramework
- Controls AssessedControls Assessed
- Assessment TypeAssessment Type
- ReportReport
- RecommendationsRecommendations
SCF 15
Exploratory
- FrameworkSCF
- Controls Assessed15 of 1000+15
- Assessment TypeExploratory
- Report
- Recommendations
SCF 50
Basic
- FrameworkSCF
- Controls Assessed50 of 1000+50
- Assessment TypeBasic
- Report
- Recommendations
NIST CSF
Alignment
- FrameworkNIST CSF
- Controls Assessed108
- Assessment TypeAlignment
- Report
- Recommendations
Others
Varies
- FrameworkVaries
- Controls AssessedVaries
- Assessment TypeVaries
- Report
- Recommendations
Exploratory Cybersecurity Assessment
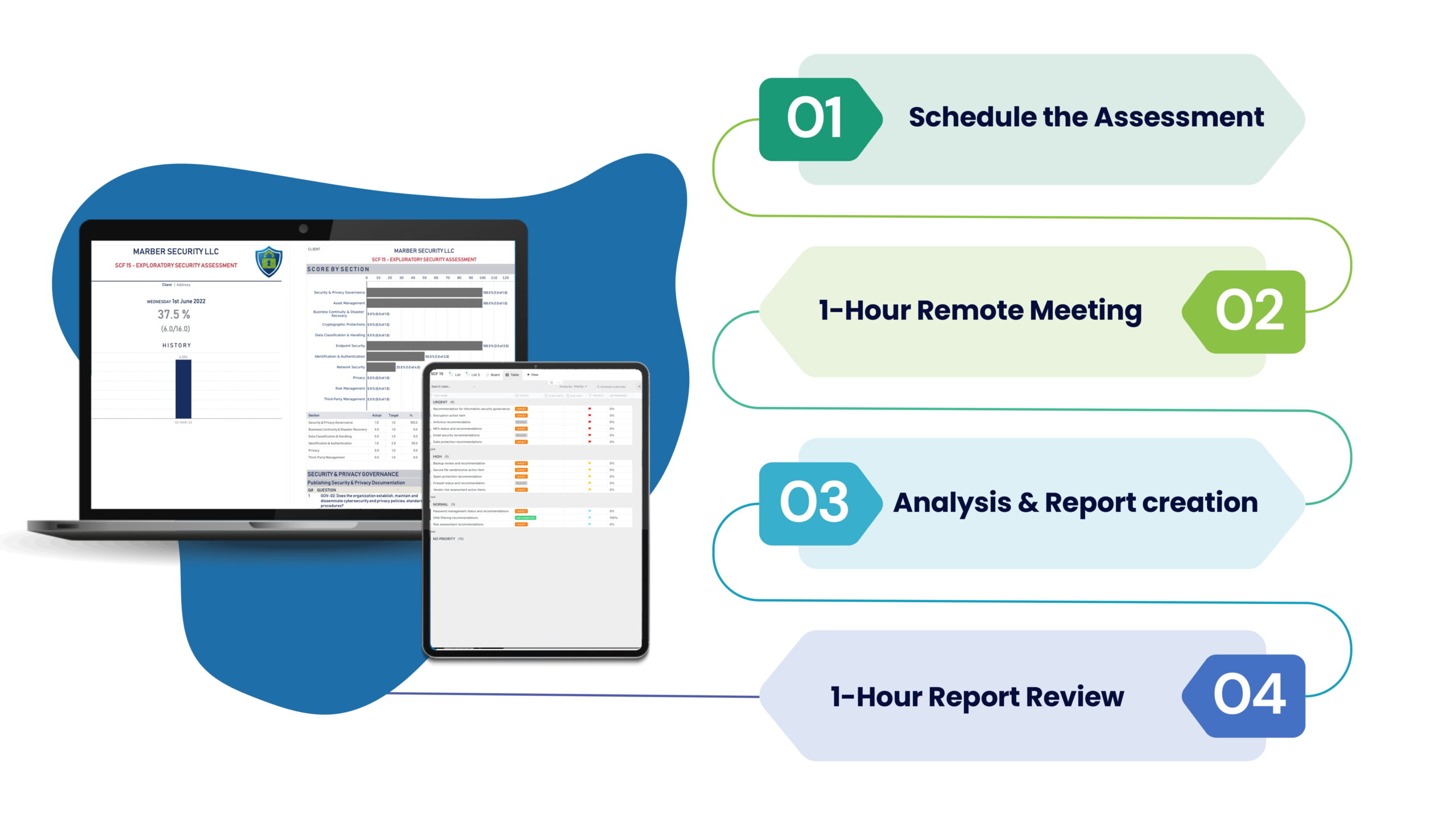
Topics covered include:
|
|

Security Assessment Methodology
The Security Assessments will follow the general principles and subcategories from the NIST Cybersecurity Framework and the recommended Security Controls will reference the NIST SP 800-53 Rev 5 Security and Privacy Controls.
General steps include
- Understand your business, how it operates, and the type of data it handles.
- Review external governance to help determine applicable requirements (laws, regulations, mandates, industry best practices, etc.), including but not limited to:
-
- State Data Privacy Laws
- HIPAA
- GLBA
- PCI DSS
- GDPR
- NIST 800-171
- Etc.
- Work with the business to define the scope of the SCF Security Assessment.
- Review existing Information Security controls:
- Administrative (policies and procedures)
- Physical
- Technical
- Identify and recommend missing critical security controls.
- Provide a report of findings and recommendations to help improve the organization’s security posture.
- Obtain the organization’s sign-off on any approved initiatives and initiate the project management phase
SCF – Security Assessments
SCF (Secure Control Framework) Security Assessments leverage some of the 1000 controls from https://www.securecontrolsframework.com/
We will work with your organization and IT department to obtain the answers to the assessment. The Deliverable includes a scored assessment with recommendations and a copy of the assessed controls and their mappings per the original SCF framework to CIS 8.0, NIST 800-53 v5, NIST 800-171 Rev 2, NIST CSF v1.1, etc. See SCF Domain Controls per SCF Assessment to review the specific SCF Controls assessed on each SCF Security Assessment.
- We will work with your organization and IT department to obtain the answers to the assessment.
- Implementation of the Security Controls is a separate billable item.
- The Deliverable includes a scored assessment with recommendations and a copy of the assessed controls and their mappings per the original SCF framework to CIS 8.0, NIST 800-53 v5, NIST 800-171 Rev 2, NIST CSF v1.1, etc.
- Please review the “SCF Domain Controls per SCF Assessment” at https://marbersecurity.com/msa/ for more details.
- Please note that the SCF Security Assessments are Basic Security Assessments, and are NOT to be deemed as a full Risk Assessment, Security Assessment, etc. Such services are available upon request.
- Visit https://marbersecurity.com/scf for a sample report
- Post-deliverable review support falls under billable “Hourly Consulting Engagements”
